What Function Describe the Uses of an Access Control List
ACLs can be used for the followingLimit network traffic in order to provide adequate network performance. Choose two a ACLs assist the router in determining the best path to a destination.
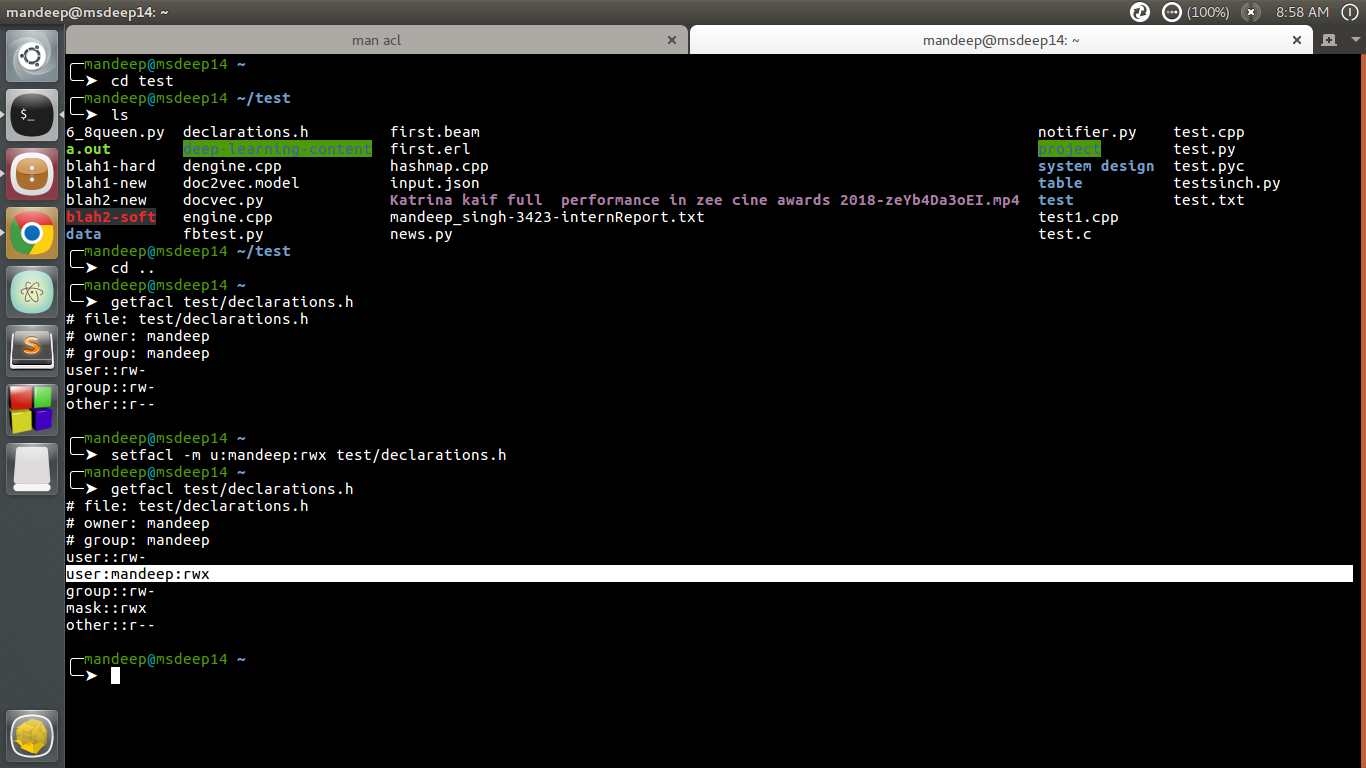
Access Control Lists Acl In Linux Geeksforgeeks
This article contains links to articles that provide details about common functions used in expressions in Microsoft Access.
. While it is important for employees to be able to access the data they need it is sometimes even more crucial that a company protects its data from outside individuals. Access control lists are used for controlling permissions to a computer system or computer network. What two functions describe uses of an access control list.
What two functions describe uses of an access control list. Filesystem ACLs filter access to files andor directories. Standard ACLs can restrict access to specific applications and ports.
Choose two ACLs assist the router in determining the best path to a destination. ACLs are used to filter traffic based on the set of rules defined for the incoming or outgoing of the network. ACLs can control which areas a host can access on a network.
When do we use Access Control Lists. ACLs can control which areas a host can access on a network. An Access Control List ACL is a set of rules that is usually used to filter network trafficACLs can be configured on network devices with packet filtering capatibilites such as routers and firewalls.
There are two types of ACLs. B Standard ACLs can restrict access to specific applications and ports. ACLs can permit or deny traffic based upon the MAC address originating on the router.
Access-list ACL is a set of rules defined for controlling network traffic and reducing network attacks. ACLs can permit or deny traffic based upon the MAC address originating on the router. ACLs provide a basic level of security for network access.
One of the most important functions of access control lists is the ability to prevent unauthorized users from accessing sensitive services or information. 1What two functions describe uses of an access control list. ACLs can control which areas a host can access on a network.
Those devices can be network devices that act as network gateways or endpoint devices that users access directly. ACLs assist the router in determining the best path to a destination. These entries are referred to as access control entities.
Standard ACLs can restrict access to specific applications and ports. Provide a basic level of security. What two functions describe uses of an access control list.
1What two functions describe uses of an access control list. ACLs can permit or deny traffic based upon the MAC address originating on the router. Choose two ACLs assist the router in determining the best path to a destination.
In this lesson youll learn more about access control lists how they function and see. It is always preferred to. ACLs provide a basic level of security for network access.
What function describes the use of an access control list. Each system object is associated with a security attribute that identifies its access control list. ACLs allow us to apply a more specific set of permissions to a file or directory without necessarily changing the base ownership and permissions.
Access control lists help organizations control how and what users have permission to access on a network. An access control list ACL contains rules that grant or deny access to certain digital environments. Restrict the delivery of routing updates.
TCO 6 What function describes the use of an access control list. Access Functions by category. Filesystem ACLs tell operating systems which users can access the system and what privileges the users are allowed.
They are used to filter traffic in and out of a specific device. ACLs are also used to restrict updates for routing from network peers and can be instrumental in defining flow control for network traffic. ACLs work on a set of rules that define how to forward or block a packet at the routers interface.
Filter traffic based on the type of traffic being sent. ACLs What two functions describe uses of an access control list. Networking ACLs filter access to the network.
Techopedia Explains Access Control List ACL File system ACL is a data structure that holds entries that specify individual user or group rights to system objects such as processes files and programs. Choose two ACLs assist the router in determining the best path to a destination. ACLs assist the router in determining the best path to a destination.
ACLs containts a list of conditions that categorize packets and help you determine when to allow or deny network traffic. ACLs can permit or deny traffic based upon the MAC address originating on. Standard ACLs can restrict access to specific applications and ports.
ACLs can control which areas a host can access on a network. They let us tack on access for other users or groups. What two functions describe uses of an access control list.
ACLs assist the router in determining the best path to a destination. C ACLs provide a basic level of security for network access. ACLs can permit or deny traffic.
ACLs assist the router in determining the best path to a destination. Access Control Lists ACLs are network traffic filters that can control incoming or outgoing traffic. ACLs provide a basic level of security for network access.
Standard ACLs can restrict access to specific applications and ports. ACLs control which user can access what services on the Internet. They are arranged first by group and then are arranged alphabetically at the end of this article.
This type of situation is what Linux Access Control Lists ACLs were intended to resolve. As I mentioned before ACLs for routers are not as complex or robust as stateful firewalls but they do offer a significant amount of firewall capability. ACLs provide a basic level of security for network access.
What two functions describe uses of an access control list.

Uploading To Amazon S3 Directly From A Web Or Mobile Application Aws Compute Blog
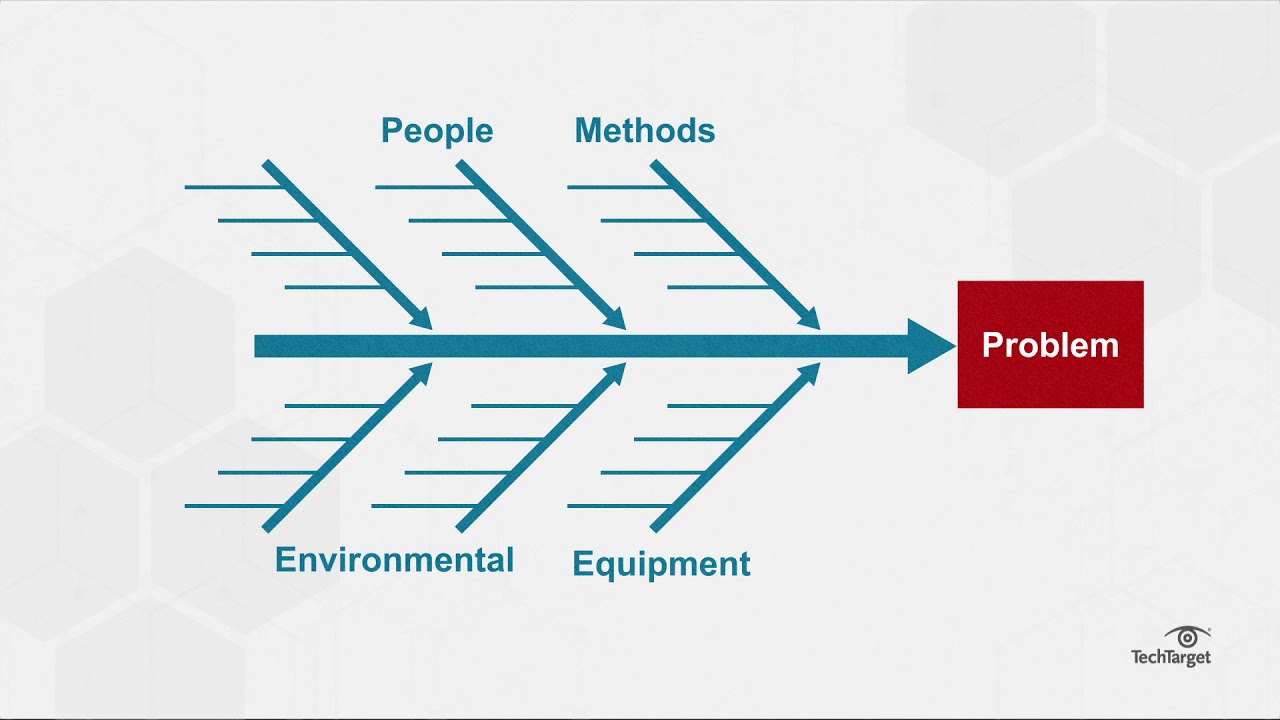
What Is A Fishbone Diagram Ishikawa Cause And Effect Diagram
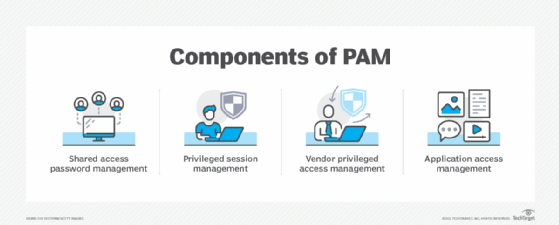
What Is Privileged Access Management Pam
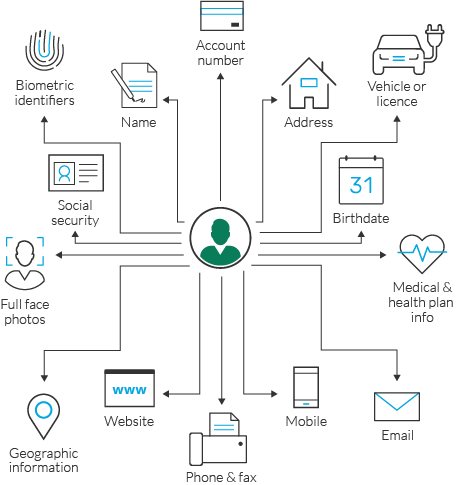
What Is Personally Identifiable Information Pii Data Security Imperva
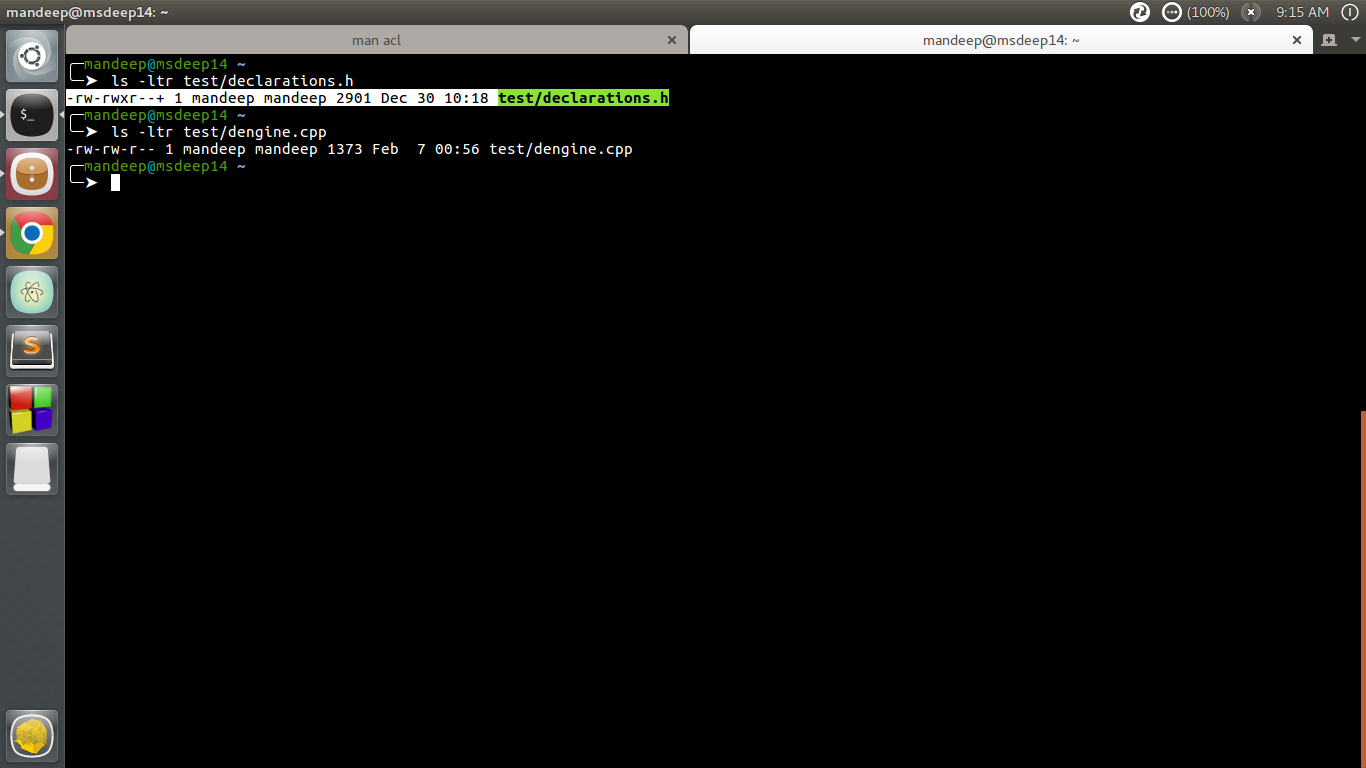
Access Control Lists Acl In Linux Geeksforgeeks
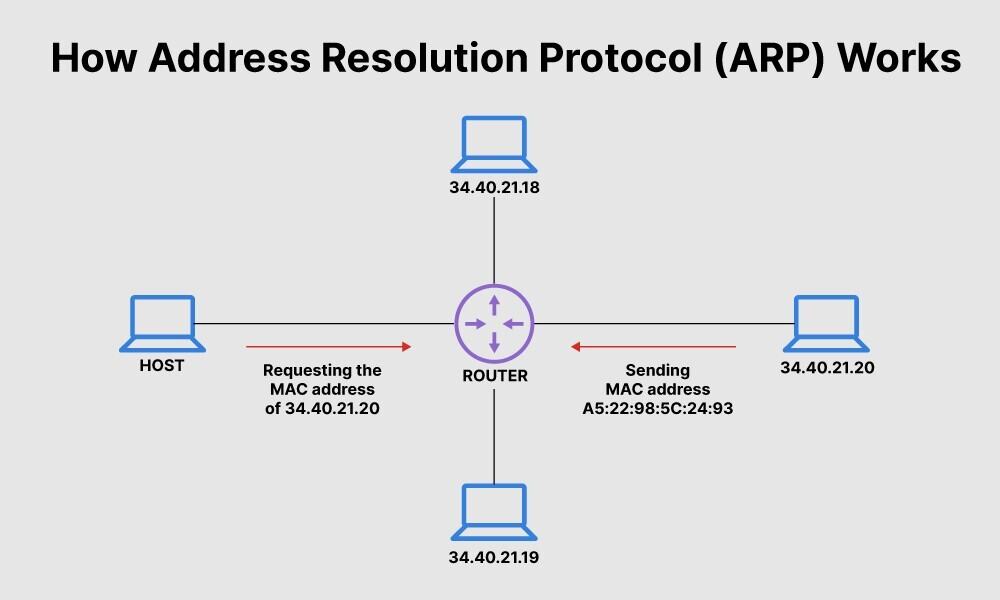
What Is Address Resolution Protocol Arp Fortinet
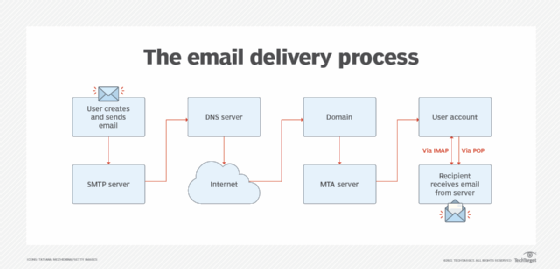
What Is Imap Internet Message Access Protocol
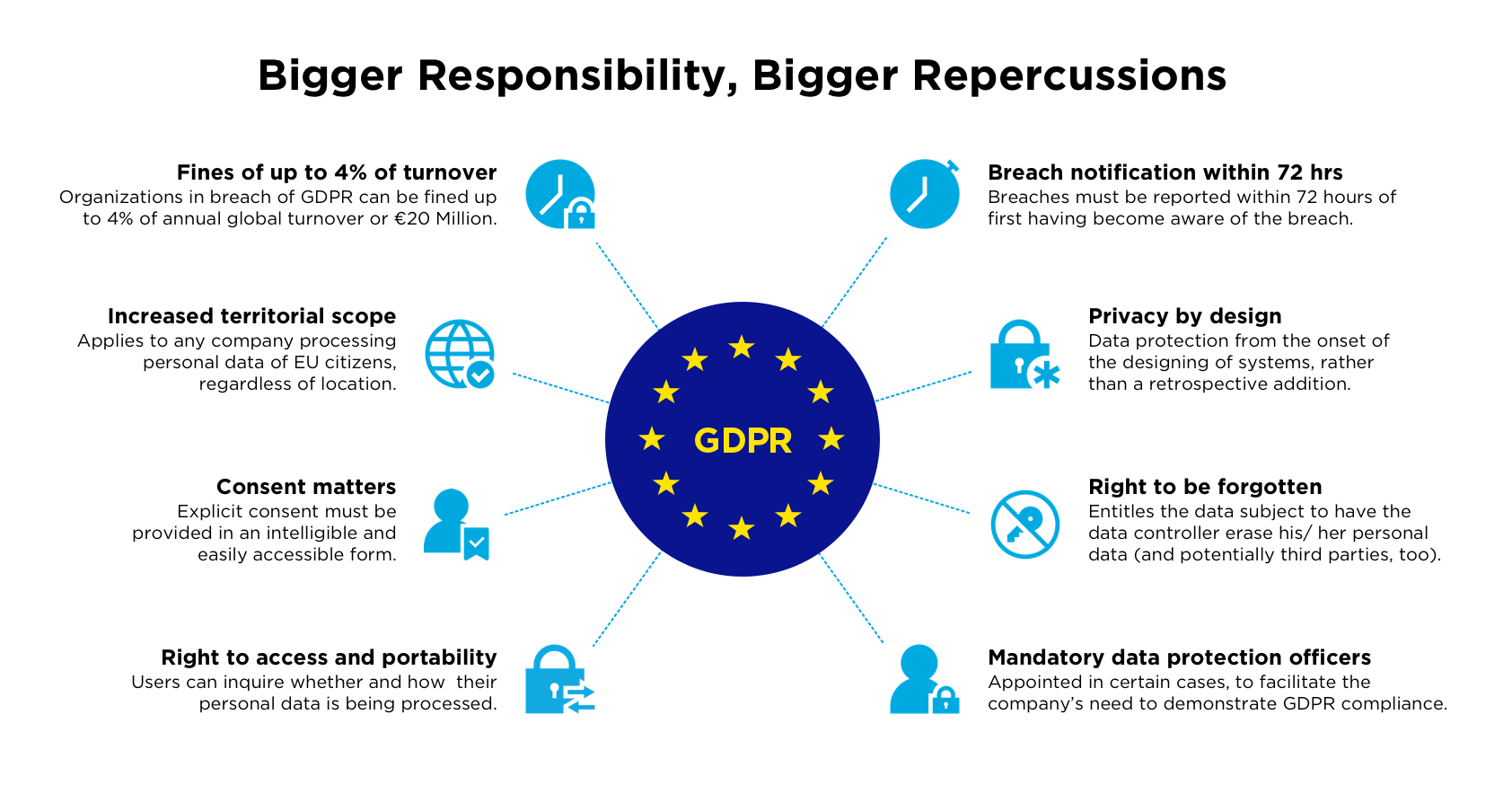
Soc 2 Type 2 Compliance Soc 2 Type 2 Report Soc 2 Audit Certification
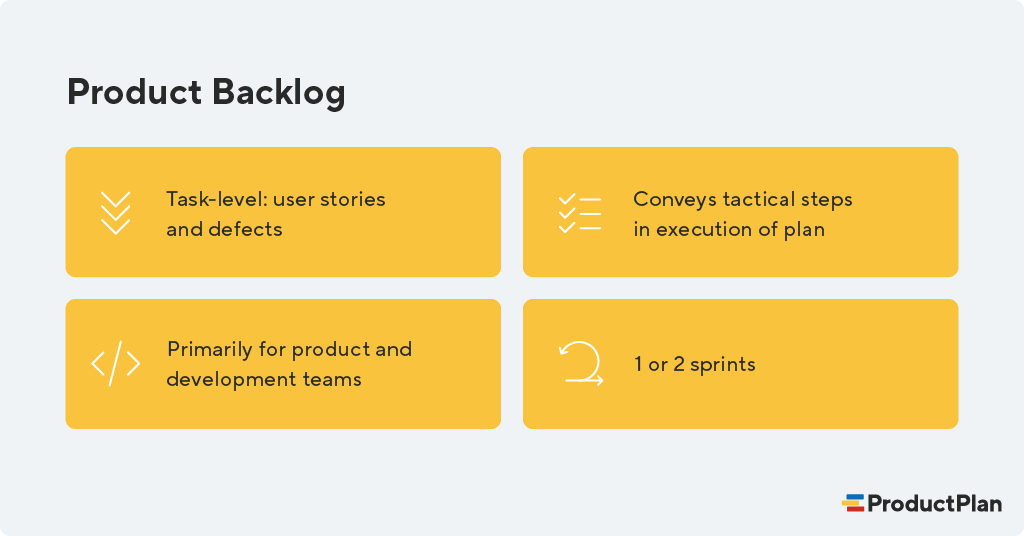
What Is A Backlog Definition Overview And Purpose

What Is Cors Cross Origin Resource Sharing Tutorial Examples Web Security Academy

Authentication Vs Authorization Okta

Common Protocol An Overview Sciencedirect Topics

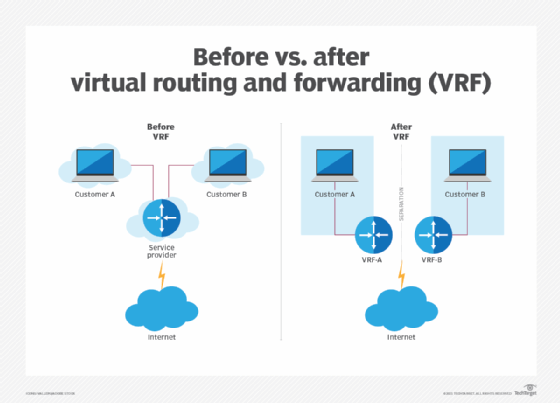
What Is Virtual Routing And Forwarding Vrf And How Does It Work

What Is Access Control List Acl Types Linux Vs Windows Imperva
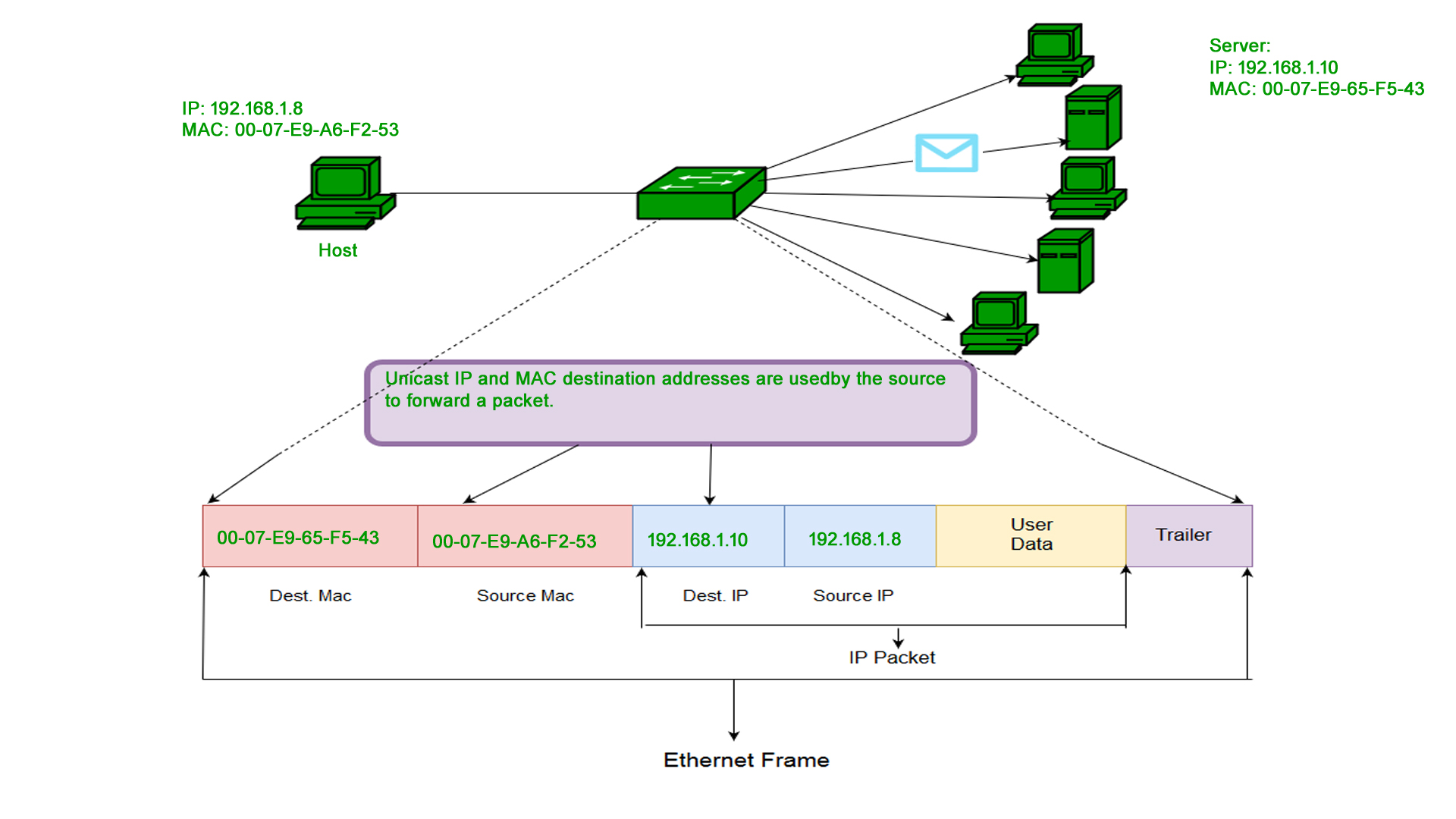
Introduction Of Mac Address In Computer Network Geeksforgeeks

Multiple Access Protocols In Computer Network Geeksforgeeks
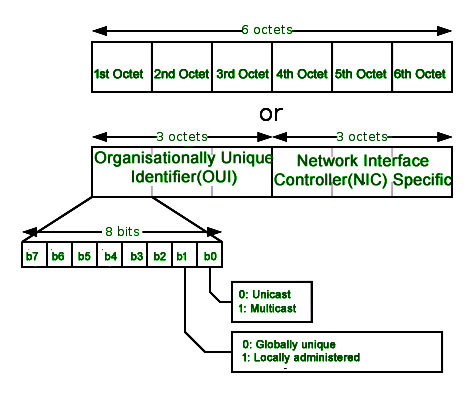
Introduction Of Mac Address In Computer Network Geeksforgeeks

Microsoft Word 2007 And 2010 Parts And Controls Office Tutorial Microsoft Word 2007 Word 2007 Microsoft Word
Comments
Post a Comment